10+ firewall diagram
The components of the Logical network shown in the above example are subnets like IP addresses masks and VLAN Id routers firewalls internet protocols routing domains traffic flow segments and voice gateways including many other network objects. Firewalls sit between a network such as the Internet and the computer or local network the firewall is protecting.

Firewalls Public Dmz Network Architecture Information Security Stack Exchange
Windows firewall action undoredo functionality default values for properties background updater improvements.

. In the example diagram above firewall rules will be added to limit the traffic between the trust LAN 1921681024 and the GUEST. More Firewall Functions. Firewall configurations that restrict outbound access to Duos service with rules using destination IP addresses or IP address ranges arent recommended since these may change over time to maintain our services high availability.
When you have an SCCM CB hierarchy with CAS and primary servers you need to be more conscious of the SCCM Firewall ports requirement. Firewall policies are used to allow traffic in one direction and block it in another direction. Top 10 Open Source Bug Tracking System.
If you get a failure a make sure your Minecraft server is indeed running on your internal. Network diagrams are often drawn with professional drawing software tools. 15 Awesome Google Search Tips and Tricks.
15 Awesome Gmail Tips and Tricks. Networking diagram and overview for Azure Red Hat OpenShift networking. -- 15 Practical Linux Find Command Examples.
10 GPS Tracker For Smartphones In Locating Missing Abducted And Kidnapped Child. 6 in diagram logontype1png Then the user will be displayed on Sophos Firewall as STAS live user. Primary authentication initiated to application or service.
The diagram above shows two Catalyst switches connected to a FDDI backbone. I have a post related to this topic that talks about SCCM Firewall port Requirements here there is not much change between SCCM Firewall ports. To use PortCheckTool simply plug in your routers public IP address in the Your IP field enter 25565 in the What Port field and click Check Your Port.
JD 4230 Wiring DiagramLooking for a wiring diagram for the wiring harness that runs up the right side of the front cab cornerConnects under the floor board and runs up under the cab to the front where it plugs in through the firewall. Logical Network Diagram Logical networks represent the flow of information in a particular network. 15 Practical Linux Top Command Examples.
The EdgeRouter uses a stateful firewall which means the router firewall rules can match on different connection states. Sophos Firewall lookups the username in AD domain controller to retrieve group email address and more details of the user. Theres only one egress policy per namespaceproject.
When intalling the appropriate switch modules and with the use of the 80210 SAID field a mapping between the Ethernet VLAN and 80210 network is created and as such all Ethernet VLANs are able to run over the FDDI network. A firewalls main security purpose for home users is blocking unsolicited incoming network traffic. 21548 views Download FREE 30-Days Norton Security Standard 2020 With Smart Firewall.
Fri Jun 10 2011 735 am Post subject. Internet access requirement or proxy exception list for SCCM CB is. There are different types of network diagrams provided by EdrawMax and you can get started with it now.
The network diagram is a schematic depicting the nodes and connections amongst nodes in a computer network or more generally any telecommunications network. 7 in diagram logontype1png User detected in such way is known as STAS logon type 1. ASAconfig show connection address 10002 16 in use 19 most used TCP outside 1985110010080 inside 1000257431 idle 00006 bytes 9137 flags UIO.
The default Pod CIDR is 101280014. In this article. RAID 0 RAID 1 RAID 5 RAID 10 Explained with Diagrams.
UML standard has no separate kind of diagrams to describe network architecture and provides no specific elements related to the networkingDeployment diagrams could be used for this purpose usually with some extra networking stereotypesNetwork architecture diagram will usually show networking nodes and communication paths between. The egress network policies are supported by using the egress firewall feature in OpenShift. Techbast has prepared a diagram situation steps to do and how to configure we will go to the next section.
Can You Top This. Attaching to Kubernetes Docker Desktop and OpenJ9 JVMs sunburst diagram for biggest objects Reactor Netty and Spring WebFlux HTTP client support Spring component detection. How To Record and Play.
The main fuse box also known as the Power Distribution Module or PDM is located under the hood on the left front fender just ahead of the bulkhead moduleThe fuses in the main fuse box are paddle type mini fusesThe battery power fuses located next to the batteries are screw-in mega fuses. The ASA is a stateful firewall and return traffic from the web server is allowed back through the firewall because it matches a connection in the firewall. First we will have an internet connection that is connected through the ISPs modem which is configured in bridge mode and configured PPPoE on the MGMT port of the Palo Alto firewall with IP 113161xx.
8825 views Top 16 Free 60 90 180 Days Antivirus Trial Norton McAfee. Jun 10 2011 Posted. Where the two harnesses plug in under the floor board a few.
Vi and Vim Macro Tutorial. As you can see in Figure 410 youll get a Success message if the website can get port 25565 traffic through your router. 2022-01-31 JProfiler Release 130.
12530 views Download FREE Norton Security Premium 2020 With 30-Days Trial. Mommy I found it. 0646d Freightliner Fld 120 Wiring Diagram Digital Resources from.
Design And Setup Cisco Juniper Fortigate Network Infrastructure By Potteralex Fiverr
Configure And Troubleshoot Router Firewall And Switches I Work On The Project By Dinesh Dabhade Fiverr

Dmz Computing Wikiwand

Firewalls Public Dmz Network Architecture Information Security Stack Exchange

Screened Subnet Wikiwand
Configure And Troubleshoot Router Firewall And Switches I Work On The Project By Dinesh Dabhade Fiverr

Johan Dahlbom Tailspintoys 365lab Net

Dmz Computing Wikiwand

Top 10 Most Popular Network Simulation Tools
%20-%20Page%201.png)
Advice Picking The Right Firewall For This Network
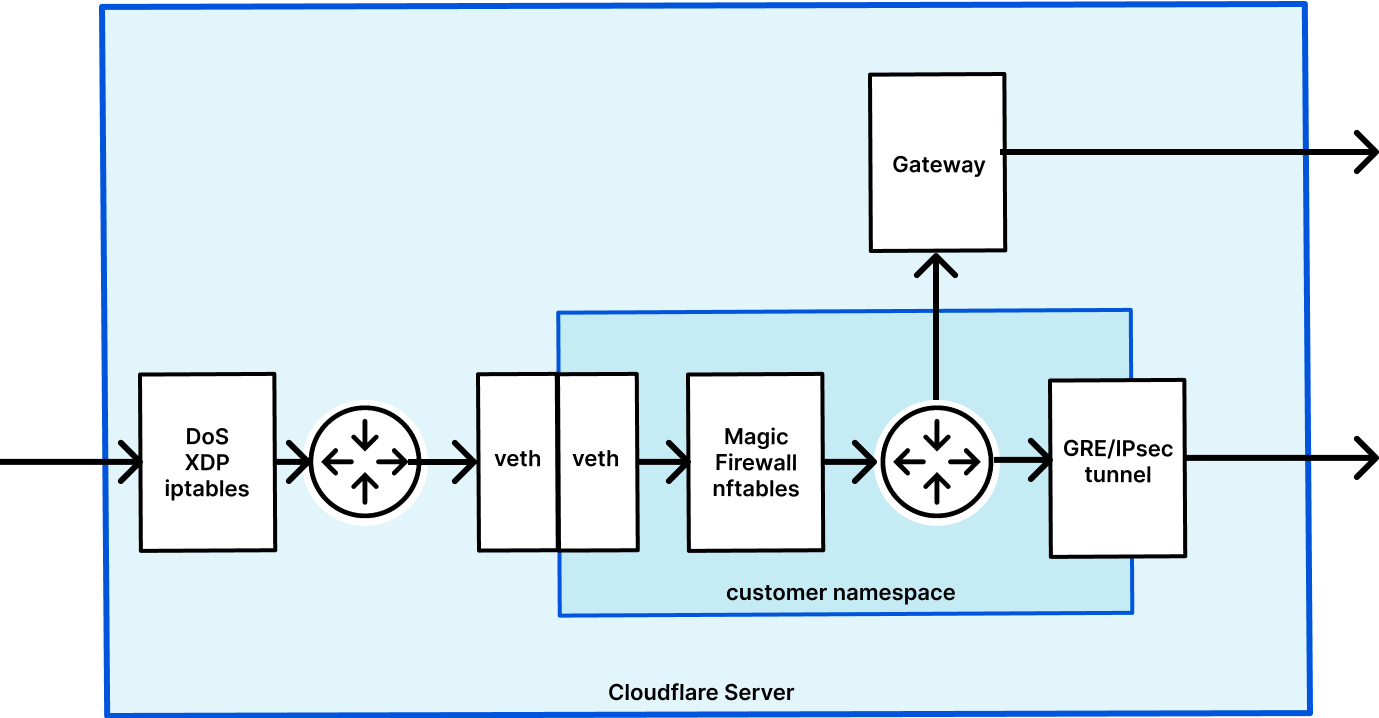
Magic Firewall Noise
Firewall Wiring Holes Jeep Enthusiast Forums

8 Ways To Detect Malicious Firewall Traffic Using Siem Blue Team Blog
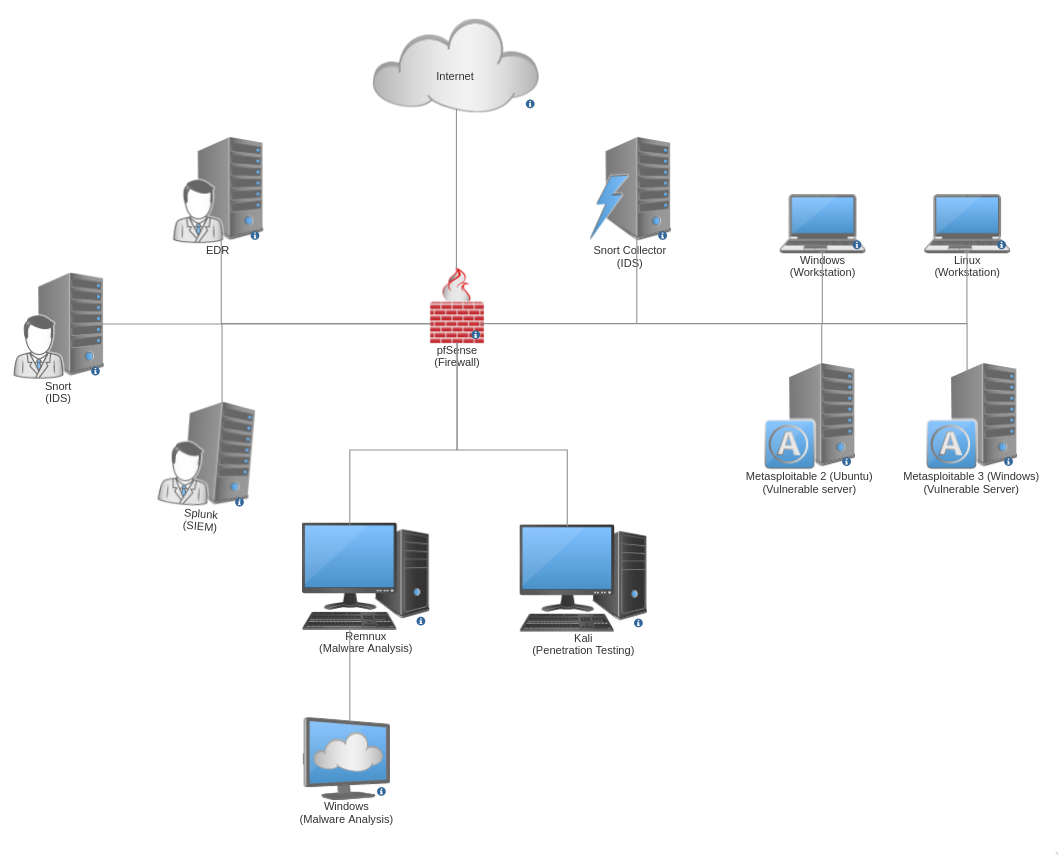
Building My Virtual Cybersecurity Home Lab
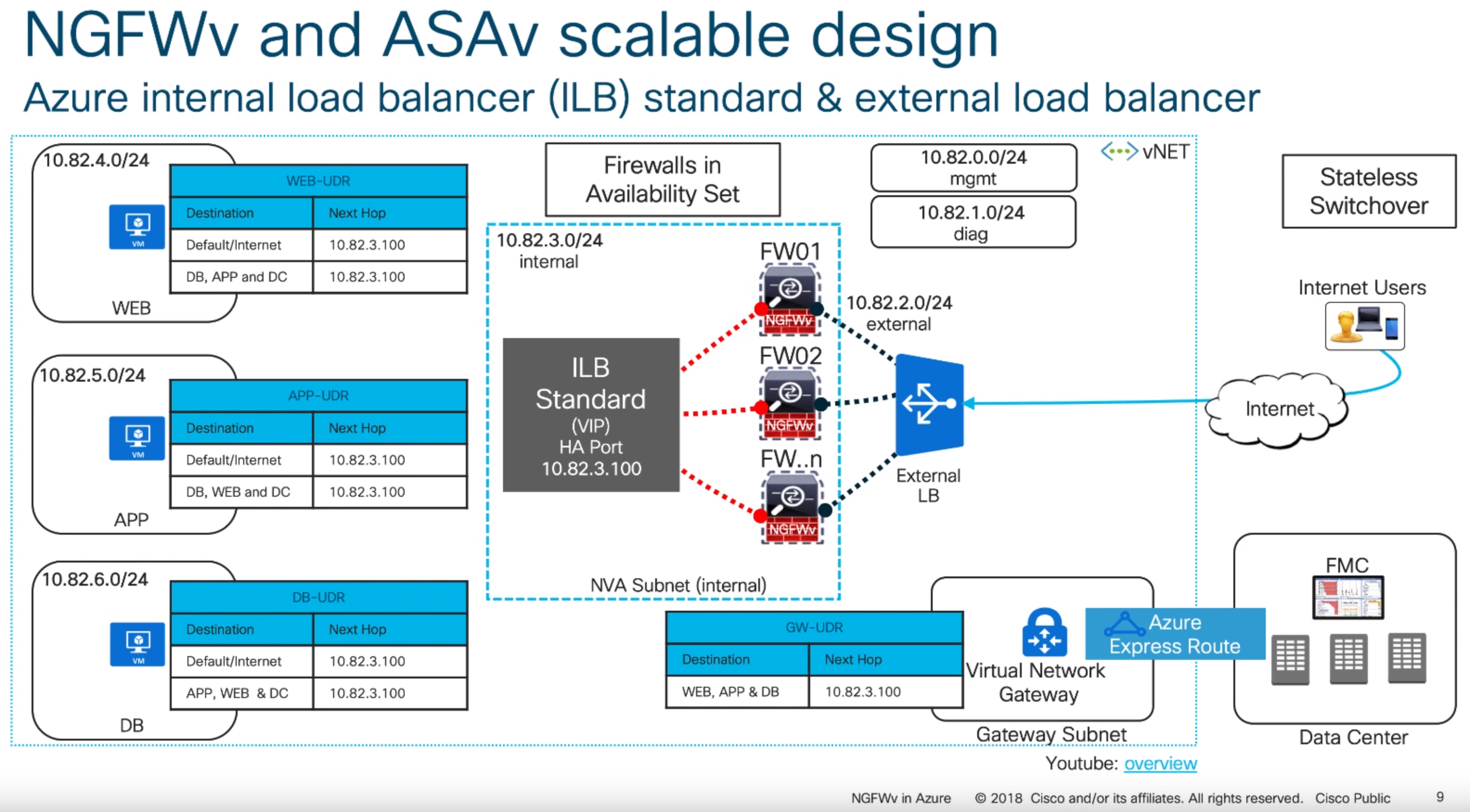
Deploying Cisco Virtual Appliances Ngfwv On Azure Jack Stromberg
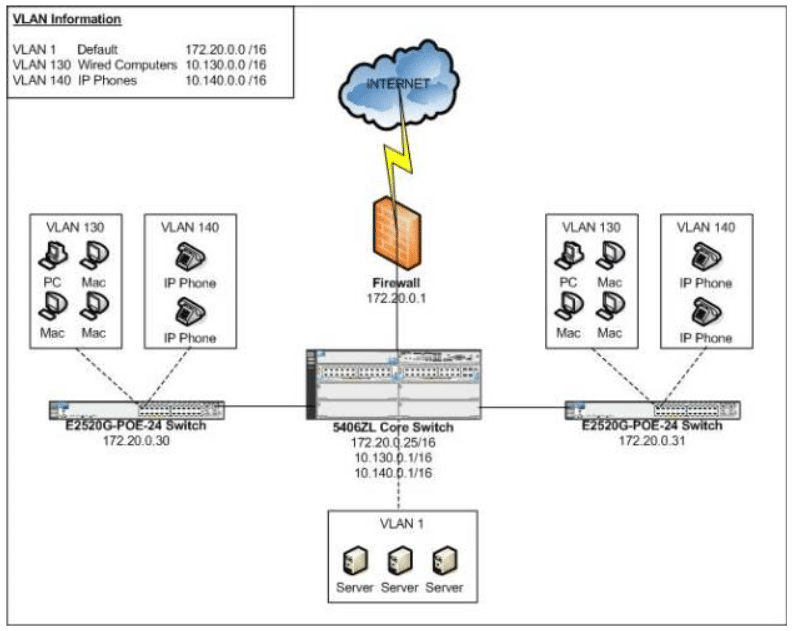
How To Deploy Hp Msm Wireless A Step By Step Guide

Load Balancing